WHAT ARE THE DIFFERENT NETWORKING DEVICES?
Network Devices
These are the devices that connect the end devices together to allow communication between hardware on computer network.
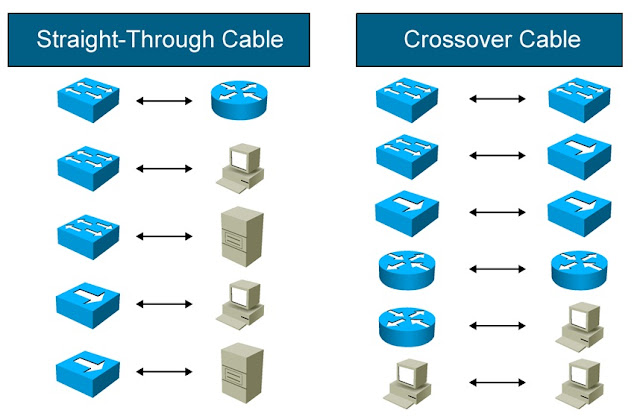
Routers, hubs, and switches are network device terms that tend to be used interchangeably. Their functions are a little different with each other even though sometimes they are all integrated into a single device.
The Hub
 |
| A hub |
A hub is a simple device that directs data packets to all devices connected to it. A hub simply provide a pathway for the electrical signals and regenerate signal before it forwards it to all connected devices.
The Switch
 |
| A switch |
Switches are the connectivity point of a wired network. Devices are connected via twisted-pair cabling, one cable for each device. The difference between the hub and the switch is how the devices deal with the data that they receive.
If a hub forwards the data it receives to all ports on the device, a switch forwards the data it receives only to the port that connects to the destination device.
The Router
 |
| A router |
As the name suggests, routers route packets to other networks until that packets ultimately reaches its destination. It can transmit both through wired and wireless networks.
A router is typically connected to at least two networks, commonly two Local Area Networks (LANs) or Wide Area Networks (WANs) or a LAN and its Internet Service Provider's network.
Other Network Devices:
The Bridge
 |
| An illustration of a bridge network device |
A bridge is used to divide larger networks into smaller sections. It is located between two physical network segments and manages the flow of data between the two. Bridges can forward data by looking at the physical address of the devices connected to each segment only if the destination address is on the another interface, however, it can also block it from crossing if verified that it is on the interface from which it came.
Types of Bridges:
a. Transparent bridge - derives its name from the fact that the devices on the network are unaware of its existence. A transparent bridge does nothing except block or forward data based on the MAC address.
b. Source route bridge - used in Token Ring networks. The source route bridge derives its name from the fact that the entire path to be taken by the packet through the networks is embedded within the packet.
c. Translational bridge - is used to convert one networking data format to another; for instance, from Token Ring to Ethernet, and vice versa.
The Network Card
 |
| Network Interface Card |
A Network Card, also called the Network Interface Card, is a device that enables computers to connect to the network.
The Modem
 |
| Modem Router |
A Modem, short for modulator/demodulator, is a device that converts the digital signals generated by a computer into analog signals that can travel over conventional phone lines.
The Transceivers
 |
| SFP transceivers |
The Transceiver is responsible for placing signals onto the network media and detecting incoming signals traveling through the same wire.
The term transceiver describe a separate network device, but it can also be technology built and embedded in devices such as network cards and modems.
Although transceivers are found in network cards, they can be external devices as well. In terms of networking, transceivers can be shipped as module or chip type.
Chip transceivers are small and are inserted into a system board or wired directly on a circuit board.
Module transceivers are external to the network and are installed and function similar to the other computer peripherals or can also function as stand-alone devices.
The Firewall
 |
| An illustration of firewall |
A firewall is a networking device that can either be a hardware or a software-based. It controls access to your organization's network. This controlled access is designed to protect data and resources from outside threat.
A typical firewall is placed at entry or exit points of a network. For instance, placing a firewall between an internal network and the Internet. When in place, it can control access in and out of that point. The firewall is configured on the server to allow or permit certain types of network traffic.

Comments
Post a Comment